Starting a 7750 SR-Seriesrouter begins with hardware initialization (a reset or power cycle). By default, the system searches Compact Flash Slot #3 (
cf3) for the
boot.ldr file (also known as the bootstrap file). The
boot.ldr file is the image that reads and executes the system initialization commands configured in the boot option file (BOF). The default value to initially search for the
boot.ldr file on
cf3 cannot be modified.
Figure 6 displays the system initialization sequence.
Figure 7 displays the compact flash directory structure and file names for the redundant chassis models.
Figure 8 displays the compact flash directory structure and file names for the 1-slot models (non-redundant).
When the system executes the boot.ldr file, the initialization parameters from the BOF are processed. Three locations can be configured for the system to search for the files that contains the runtime image. The locations can be local or remote. The first location searched is the primary image location. If not found, the secondary image location is searched, and lastly, the tertiary image location is searched.
If the BOF cannot be found or loaded, then the system enters a console message dialog session prompting the user to enter alternate file locations and file names.
The boot.ldr can be interrupted during the boot sequence by pressing any key on the CPM console port. The operator must then type
sros and press
ENTER within 30 seconds or the
boot.ldr will continue trying to boot the system. This key sequence ensures that noise or misconfiguration does not inadvertently interrupt the boot sequence. If the operator types
sros and presses
ENTER within 30 seconds, they are brought to a console message dialog session prompting the user to enter file locations and other boot information.
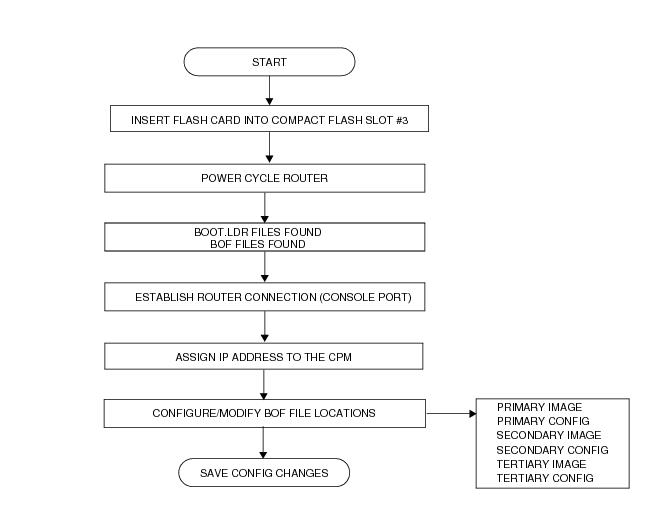
Figure 9 displays the boot sequence.
Optionally, the BOF persist parameter can specify whether the system should preserve system indexes when a
save command is executed. During a subsequent boot, the index file is read along with the configuration file. As a result, a number of system indexes are preserved between reboots, including the interface index, LSP IDs, path IDs, etc If persistence is not required and the configuration file is successfully processed, then the system becomes operational. If persist is required, then a matching
x.ndx file must be located and successfully processed before the system can become operational. Matching files (configuration and index files) must have the same filename prefix such as
test123.cfg and
test123.ndx and are created at the same time when a
save command is executed. Note that the persistence option must be enabled to deploy the Network Management System (NMS). The default is off.
Figure 10 displays the process start your system. Note that this example assumes that the boot loader and BOF image and configuration files are successfully located.